Security Operations Center: SOC Ultimate Business Guide
Security Operations Center: SOC Ultimate Business Guide
Challenges Maintaining An Effective Cyber Security Response
All businesses are facing challenges maintaining an effective cyber security response, which is why SOC essential to your cyber-risk strategy. A SOC is a strategic foundation that enables a business to react and make decisions to mitigate cyber security risks.
Taking a read of this years Global Cyber security Outlook 2022 Report by the World Economic Forum, Nancy Luquette Global, Chief Risk and Compliance Officer, S&P Global says it best:
“Looking ahead to 2022-2023, cyber-security must be seen as a strategic business issue that impacts decision-making. To mitigate risks like ransomware and social engineering, organisations must ask not simply how they are protected, but how well – with an eye to strength, sophistication and efficacy.”
Digging into this further organisations are presented with tackling the following four challenges:
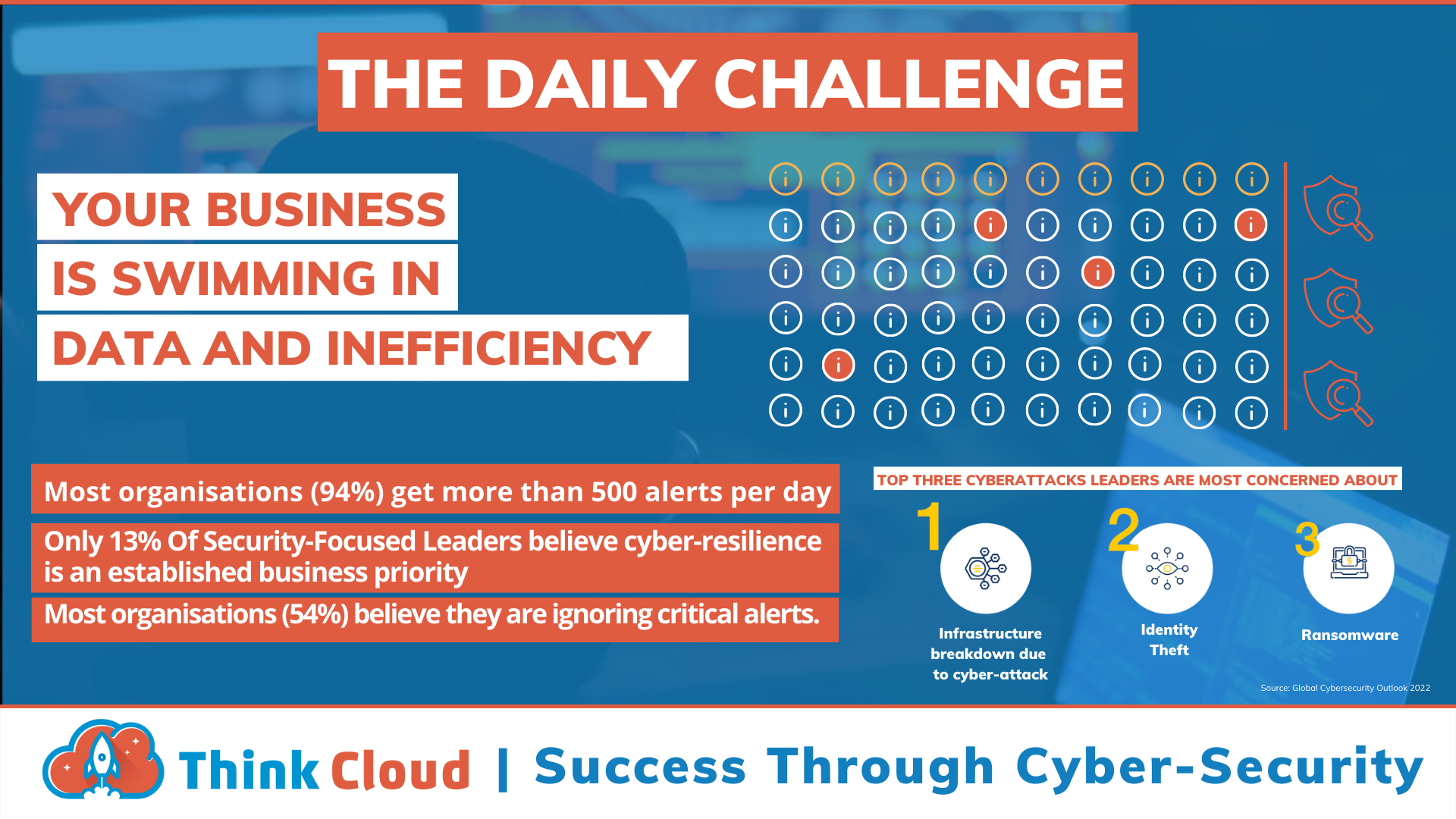
Notification Fatigue
Being overwhelmed with security alerts is a common challenge. In order to properly categorise and prioritise them, you need both advanced systems as well human oversight - but when there are too many threats present in your network or system (which can happen), then these tools are not enough on their own! You also require an expert team who understands how to identify and mitigate the risks faced.

Complexity
High-risk attack surfaces have been made more complex by the global nature and fluidity of business. Simple solutions like firewalls are no longer enough to keep attackers from breaking into your systems, which is why cyver-security today requires both technology and people in addition to processes! This can be difficult for some companies who want an easier solution - but this comes at a cost: poor security will likely result if you choose poorly because it's hard (and expensive) work keeping up with the pace of change. Covid-19 was great at moving business into the cloud but poor at helping us secure it.
Costs
The cyber security field is a highly specialized one, and it can be difficult for an organisation to maintain their own cyber-security. In addition the threat landscape changes constantly which requires frequent updates as well continuous learning from staff members about new threats and vulnerabilities. Maintaining a SOC takes time away from other important objectives like growing sales revenues by developing innovative products.
Cyber Security Skills Shortage
The world is lacking 3 million cyber security professionals, latest report by the World Economic Forum (WEF). Cyber Security skills are in high demand — Recruiting and retaining cybersecurity talent is a huge challenge for businesses. In the recent by WEF survey found that 59% of all respondents would find it challenging to respond to a cyber security incident due to the shortage of cyber security trained within their teams.
Outsourcing your cyber security helps organastions solve these challenges.
What Does A Security Operations Center Do?
In today's increasingly connected world, where organisations are constantly collecting and storing more data than ever before, having a robust and effective security operation centre cannot be underestimated. With the right tools and personnel in place, the security operation centre can help to protect an organisation's most valuable assets and ensure that its data and systems are safe from harm.
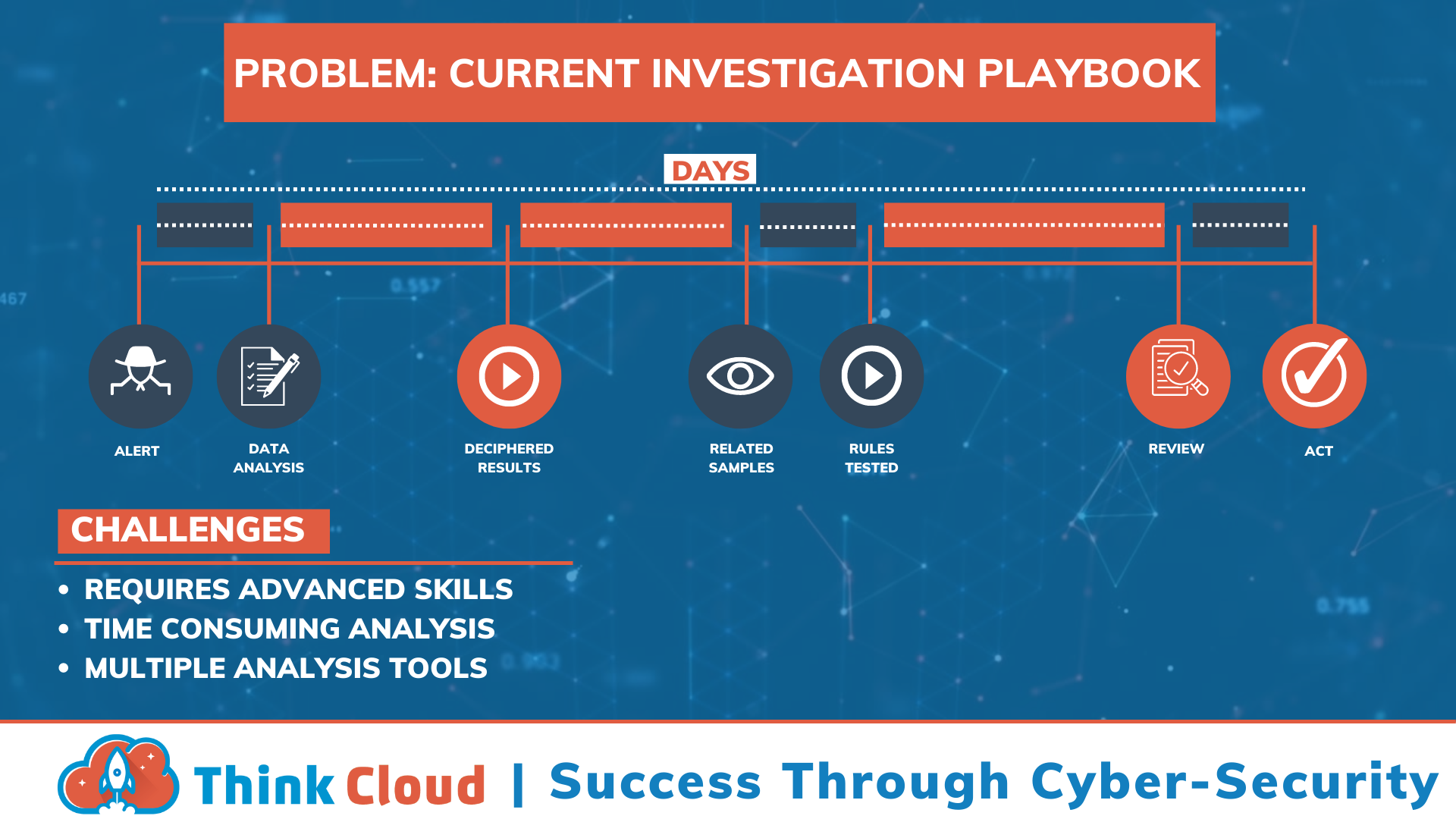
When it comes to cyber security, a Security Operation Center (SOC) is a vital component for any business. A SOC brings together skilled security personnel, processes and technologies to continuously monitor for malicious activity and prevent, detect and respond to cyber incidents by deploying, managing and updating security technologies and tools key to securing your data.
We think of our SOC as a command center that gathers data from across an organisation's IT infrastructure, including network devices, computers, and cloud applications. Over the last ten years, cyber threats have prompted businesses to take a layered approach to security, resulting in many point solutions producing massive amounts of threat data for monitoring. You can not manage cyber risk without such analysis, as it can help organisations focus on the most critical threats and better understand their risk exposure.
Here Are 11 Of The Most Important Reasons To Have A SOC:
1. Centralised command: Our SOC is a unified command center that gathers data from our client's IT infrastructure, including network devices, PCs, and cloud applications.SOCs can help organisations adopt a more thorough approach to cyber security risk management, resulting in generating large amounts of threat data to monitor.
2. Log management and analysis is a crucial function of the SOC, as it helps identify trends and anomalies that may indicate a security breach. By centralising log data from across the network, the SOC team can more easily spot potential threats and take appropriate action to mitigate them.
3. Storage retention policies are also managed from the SOC, ensuring that relevant logs and other data are kept appropriately based on regulatory or your business requirements.
4. Decreased costs: With an outsourced cyber-security service which includes a SOC, you can get immediate access to cyber-security expertise without spending money on recruiting, retaining and managing staff let alone having to manage to cyber-security tools needed to power a SOC. It also helps to mitigate the financial consequences of a cyber attack, as SOCs shorten the dwell time, resulting in decreased financial costs when an attack does happen. By consolidating all security monitoring and logging into a single location, organisations can reduce overall technology investments and have a fixed price solution.
5. Threat prevention: The SOC enables our clients to gain a more robust cyber-security posture by allowing our experts to identify and counter threats before they harm them. The SOC also can isolate and contain the threat until it can be fixed or removed. Threat correlation and analysis and real-time monitoring and detection capabilities are essential functions of a Security Operation Centre, helping to identify and mitigate risks promptly and protect critical business data from being compromised or stolen. Additionally, a SOC can also improve network visibility by providing details about suspicious activities occurring on the network.
6. Communication and collaboration: SOCs can help organisations focus on the most critical threats and better understand their risk exposure.
7. Compliance requirements: In many industries, compliance regulations are necessary. A SOC helps organisations meet and comply with regulatory compliance requirements by providing an audit trail of all activities related to the security of data and systems.
8. Quick and effective response: Your outsourced cyber-Security should have an existing stack of Cyber Security technologies at hand, including firewalls, antivirus, email security and screening, DNS, authentication, etc. Our SOC supports the existing layers of protection we include in our cyber-security solution and delivers immediate insight and compatibility, detecting and mitigating threats in real-time across your network.
9. Continuous protection: Our SOC teams employ several tactics to keep track of threats. Continuous monitoring is vital to detecting the earliest indications of ma behaviour. Attacks are not just limited to Monday through Friday from 9 to 5. Whether in-house, hired, or virtual, SOC team members are on hand to check for potential vulnerabilities 24 hours a day, every day, to detect attacks.
10. Remote home worker coverage: During the pandemic, many organisations had to rapidly adapt to remote working with hybrid working being here to stay. This has resulted in an increased reliance on cloud-based systems and applications, which present new cyber security risks. A Security Operation Centre can provide remote coverage for these home workers, helping to reduce any potential cyber-risks.
11. Forensic investigation of past cyber security incidents is also made easier with a Security Operations Centre, as all the relevant data is stored in one place, allowing analysts to more quickly and thoroughly investigate security incidents.
Roles and Responsibilities in our SOC Team
The Cyber security Operations Center (COC) is the digital front line of defense against cyber attacks. They are usually made up mostly by security analysts, threat hunters and networking professionals with backgrounds in computer engineering or data science who have been trained on how to fight back through different methods such as analytics for detecting intrusions before they become an issue, and cyber threat hunting for proactively finding compromises and cyber risks.
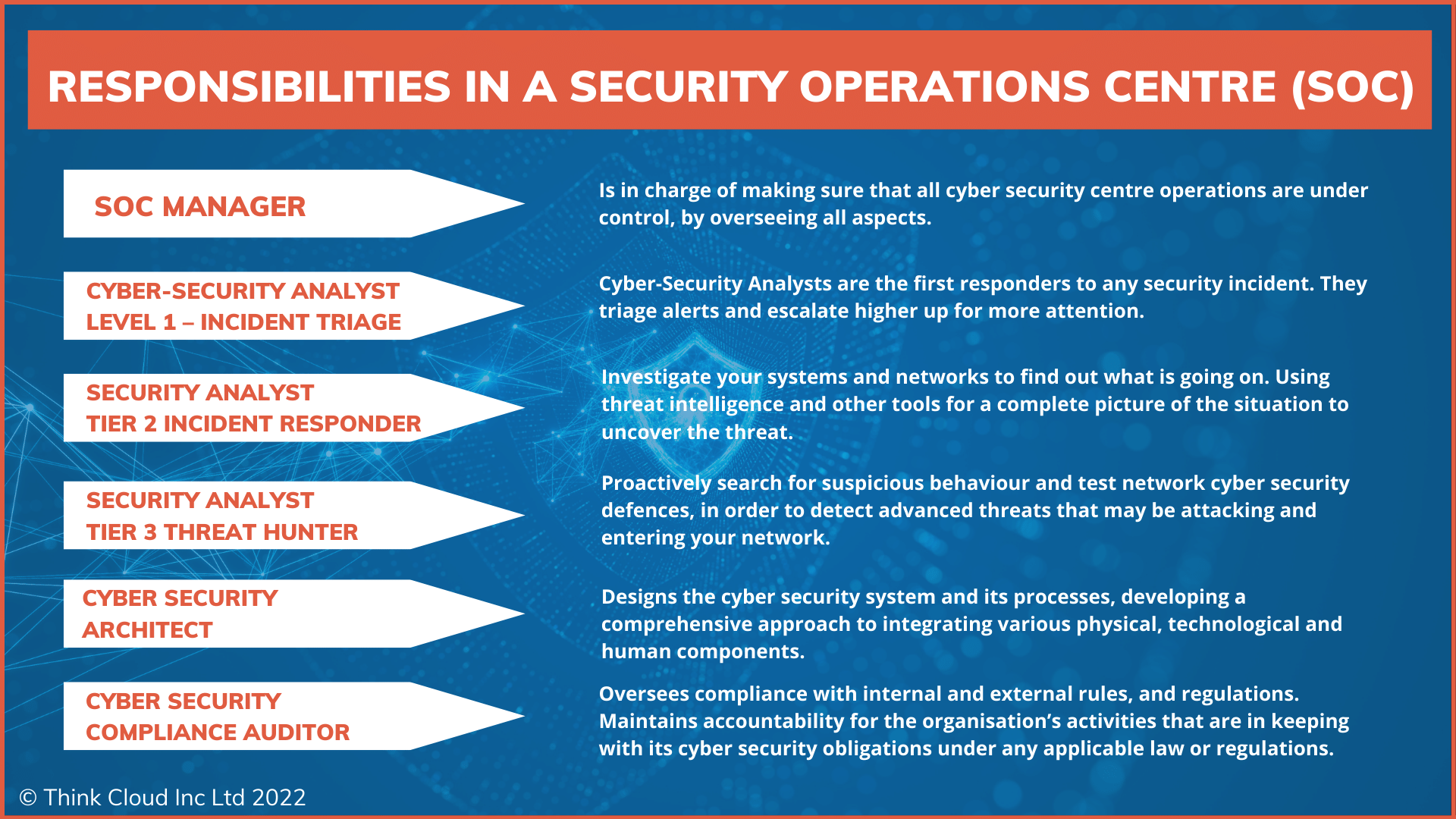
The Cyber security teams' duty is to keep networks safe from cyber attacks. They check for vulnerabilities and monitor the flow of data within an organisation's IT infrastructure. To do this, they look at logs that might provide hints about possible intrusions as well as examining how quickly systems respond when something does go wrong. The team roles within a SOC are:
Security Operations Centre Manager: is in charge of making sure that all operations are under control, by overseeing all aspects
Cyber Security Analyst Level 1 – Incident Triage: Cyber Security Analysts are the first responders to any security incident. They triage alerts and escalate higher up for more attention.
Cyber Security Analyst Level 2 – Cyber Incident Responder: Investigate your systems and networks to find out what is going on. Using threat intelligence and other tools for a complete picture of the situation to uncover the threat.
Cyber Security Analyst Level 3 – Cyber Threat Hunting: Proactively search for suspicious behaviour and test network cyber security defences, in order to detect advanced threats that may be attacking and entering your network. They assess areas where vulnerabilities exist or protect assets insufficiently protected by current measures.
Cyber Security Architect: Designs the cyber security system and its processes, developing a comprehensive approach to integrating various physical, technological and human components.
Cyber Security Compliance Auditor: Oversees compliance with internal and external rules, and regulations. Maintains accountability for the organisation’s activities that are in keeping with its cyber security obligations under any applicable law or regulations.
Conclusion: A SOC Strengthens your Defence Against Cyber threats.
If you're not already convinced of the importance of having a SOC, hopefully, this list has given you something to think about. A Security Operation Centre can be a vital component for any business regarding cyber security. By deploying a SOC, companies can take a proactive approach to cyber-security instead of waiting for an attack to happen.
A SOC is a valuable asset for any business, big or small. So if you're looking to bolster your cyber security defences, it should be on your radar.
In summary, a Security Operations Centre provides an essential service for any organisation that relies on computers and networks to function. It helps to keep sensitive data and systems safe and makes it easier to respond quickly and effectively to any incidents.
Every 11 seconds a small business in the United Kingdom is hacked successfully, with 51 per cent of those affected reporting being hit by Ransomware. Stop and consider this: 60% of small businesses close within six months after cyber crime attacks!
We are positive that we can protect you from this outcome, so there’s no time to waste.
When Was The Last Time You Had A Cyber Risk Assessment?
If you're wondering what are the benefits of having Our Outsourced Cyber Security Protection check out how we can help your organisation today!
We also provide comprehensive cyber security training, and have made our key courses free to all UK Organisations learn more now!
Don't Be A Sitting Duck; things Have Changed. Cyber Attacks Are Up! Learn how to stop the hackers including the secrets to protecting your business. Take-free training today
Free - Sign up for our free Cyber Security Master class + Learn how to Reduce your Human Cyber Risk here
Tagged as: Cyber Security, Insights
Share this post:

